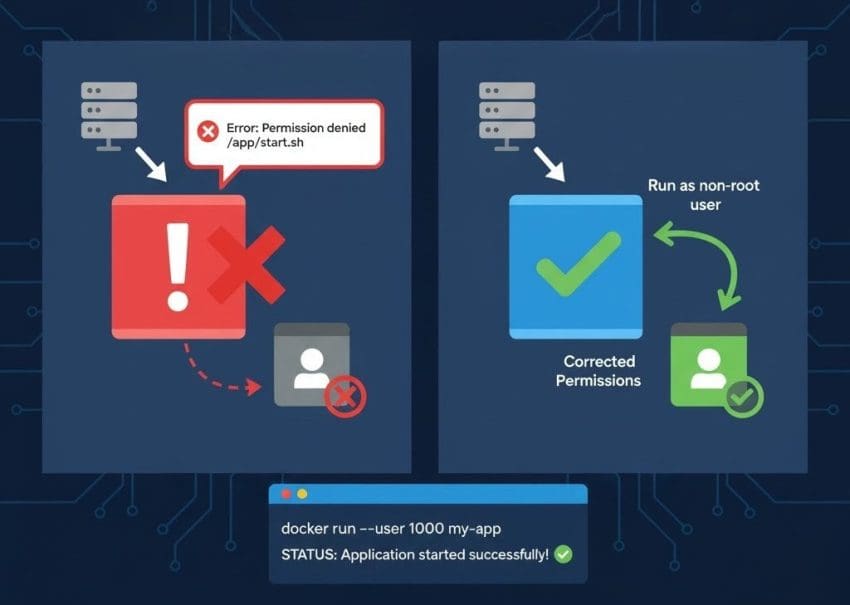
A common issue encountered while containerizing applications is when the app runs perfectly on a local machine but crashes inside a container with a “permission denied” error. This behavior often confuses engineers since the same steps work outside the container but fail within it.
🔍 Understanding the Root Cause
The main reason behind this issue lies in how user permissions differ inside containers.
When testing an application locally, it’s usually executed under a user account that has elevated privileges — for example, a system user with ownership rights over files and directories. However, Docker containers typically run processes under restricted users, not root, for security reasons.
Inside the Dockerfile, a non-root user (such as appuser) is often created to run the application. If this user doesn’t have sufficient permissions to access or execute the required files, the containerized application fails with a “permission denied” error.
⚙️ How to Fix the Issue
To resolve this, ensure that the files and directories inside the container have the appropriate ownership and permissions:
1️⃣ Grant execute permission to the application file:
chmod +x app.py2️⃣ Change ownership of the directory or files to the correct user:
chown appuser:appuser /appThese commands ensure that the container’s user (in this example, appuser) can access and execute the necessary files.
🧩 Best Practice Insight
Before building a Docker image, it’s essential to understand the build process of the application. Developers often use environments like Ubuntu or their local machines, where their users already have full access. When translating that setup into a container, permission differences can arise if the Dockerfile doesn’t properly handle user setup and file access.
A good practice is to verify permissions within the Docker image before running the container by checking ownership with:
ls -l /app🚀 Wrapping It Up
“Permission denied” errors in containers are not uncommon but are easy to fix once the cause is understood. Ensuring that the containerized application files are owned and executable by the correct user prevents such issues from recurring. Proper permission handling also strengthens container security by avoiding unnecessary use of the root user.
To dive deeper… Check out these related topics: